
Onar Alili
Engineer
5 minutes to read
The Tricks Spammers Use to Fool CAPTCHAs
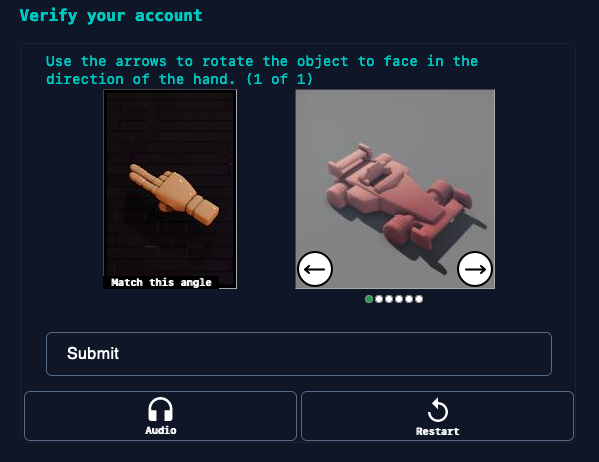
You’ve probably encountered those annoying little puzzles that websites make you solve before letting you in – you know, the ones where you have to select all the images with traffic lights or type out some distorted text. Yeah, those are CAPTCHAs, and they’ve been around since the early 2000s as a way to keep bad bots and hackers out of websites.
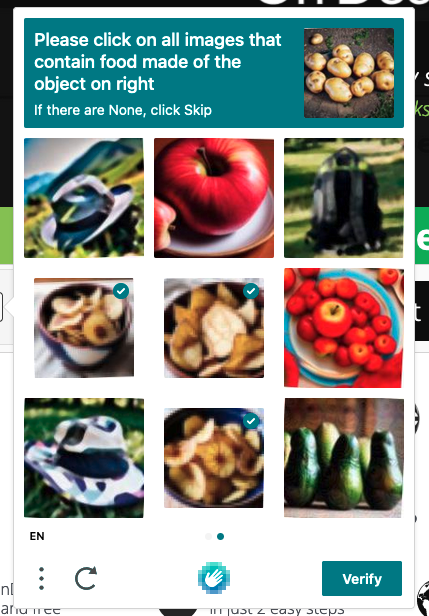
But here’s the thing – after over two decades of battling these security tests, spammers have become total pros at cracking them. In fact, recent research shows that a whopping 50% of CAPTCHAs are now being solved by bots, not actual humans! Crazy, right?
So, what does this mean for you and your website? Well, it means that those bots controlled by attackers can easily bypass your CAPTCHA defenses and spam your comments section, submitting fake forms, or abusing other services on your site.
To really understand what’s going on here, let’s break down how CAPTCHAs work and how these CAPTCHA solver services manage to bypass them so effortlessly.
Basically, a CAPTCHA is like a little test for your website visitors to prove they’re human and not a robot. It could be something as simple as typing out some funky-looking text or identifying specific objects in a set of images. The idea is that while humans can easily solve these puzzles, bots and other automated systems can’t. Even the more modern “Invisible CAPTCHAs” that don’t require solving puzzles aren’t safe - they work on the same fundamental principles.
There are many reasons why someone would want to bypass CAPTCHAs like hCAPTCHA, reCAPTCHA, Turnstile and many others. Not all of them are malicious. Some non-malicious reasons include browser automation with Selenium, UI and form testing. Unfortunately, spammers also use similar techniques to circumvent CAPTCHAs. That’s why your signup, newsletter, or contact forms are still being bombarded with spam even though you have a CAPTCHA in place.
But here’s where things get tricky…
CAPTCHA Solving Services
Believe it or not, there are services like 2Captcha and Capsolver that employ humans and advanced computer vision algorithms to solve CAPTCHAs. Spammers simply pay these services to bypass CAPTCHAs at scale.
CAPTCHA Farms
Some spammers go old-school and set up “CAPTCHA farms” where they hire cheap labor, often exploiting people in developing countries, to manually solve CAPTCHAs in bulk.

Computer Vision Attacks
These days, advanced computer vision and machine learning techniques can be used to build systems that can accurately solve text, image, and audio-based CAPTCHAs automatically. Spammers are always keeping up with the latest tech.
Re-Using CAPTCHA Solutions
Some CAPTCHA implementations cache solutions client-side, allowing spammers to re-use previously solved CAPTCHAs. It’s like having a master key to bypass the system.
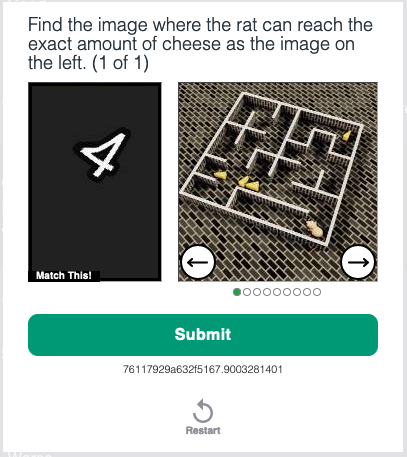
Exploiting Implementation Flaws
Spammers are always on the lookout for flaws or vulnerabilities in how a CAPTCHA is implemented on a website. If they find a loophole, they’ll exploit it to bypass the system.
Targeted Attacks
These sneaky spammers study the patterns and characteristics of a specific CAPTCHA implementation to develop targeted attacks catered towards bypassing that exact system.
Botnets
Massive botnets comprising thousands of compromised machines can be leveraged to slowly solve CAPTCHAs over time through brute force. It’s like having an army of robots working for you.
Social Engineering
Sometimes, spammers trick real humans into solving CAPTCHAs by disguising malicious sites or forms as legitimate ones. It’s like a digital con game.
Why CAPTCHAs are Vulnerable by Design?
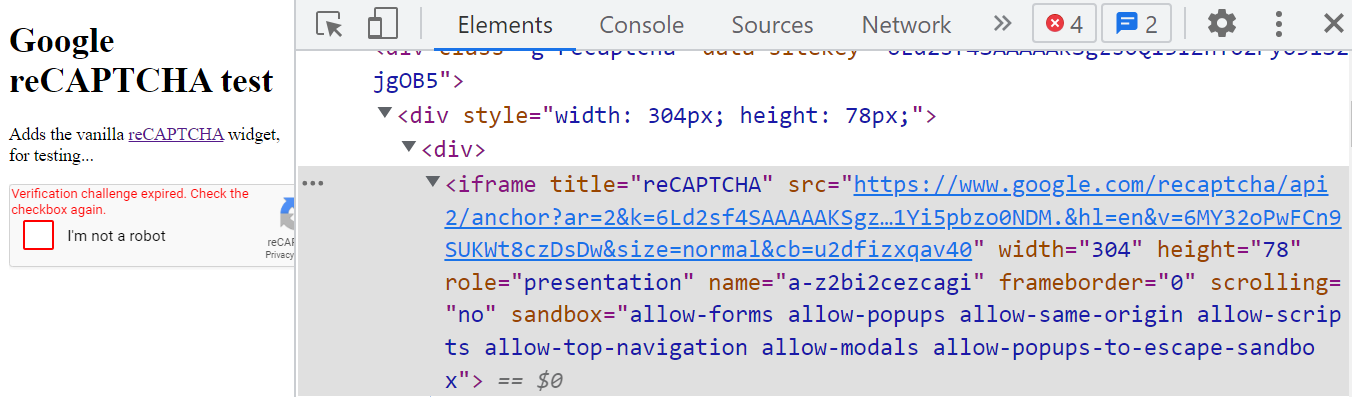
Regardless of how complex the puzzle or background calculation in the CAPTCHA solution you’re using, they come with a fundamental issue that makes them easy to manipulate: they are client-side solutions. This means that spammers can manipulate the Document Object Model (DOM), obtain your site key from the website’s HTML source, solve the puzzle, and paste the generated response back to the website.
Another issue, at least with the puzzle version of CAPTCHA solutions, is inaccessibility and privacy concerns. They can be challenging to solve for many users, and some CAPTCHAs even track your visitors’ behavior, raising privacy issues.
It’s ironic that CAPTCHAs are increasingly becoming harder for people to solve but easier for bots to crack.
Alternative to CAPTCHAs?
The fact is, spammers have an entire bag of tricks to bypass those CAPTCHAs. They’re constantly evolving and finding ingenious new ways to outsmart these security measures. That’s why it’s absolutely critical for CAPTCHA systems to stay ahead of the game with frequent updates. But even then, website owners can’t rely solely on CAPTCHAs - they need to bring in extra reinforcements in the fight against spam.
That’s where alternative ways like OOPSpam can make the difference. Instead of interacting with your visitors, OOPSpam works its magic behind the scenes, on the server-side. So even if a bot manages to crack through your CAPTCHA defenses, OOPSpam has your back. It cross-checks every IP address, email, and message against a massive database of millions of known malicious activities. With this added layer of abuse detection, you can drastically reduce spam.