
Chazie Baniquid
Technical Content Marketer
4 minutes to read
How to Block VPN and Data Center IP Submissions in MetForm?
MetForm cannot block VPN or data-center IPs by itself. To stop anonymous network abuse, you must add a security layer, either at the form level (OOPSpam) or at the network edge (Cloudflare Firewall).
Below are the simplest and most reliable methods for MetForm users.
Why MetForm Needs Help Blocking VPN and Data Center IPs
Attackers hide behind VPNs and cloud-server IPs because they want anonymity. MetForm does not detect these sources by default. Modern spam networks use:
- Cloud data centers (AWS, Google Cloud, Azure, OVH, Hetzner)
- Proxy/VPN services
- TOR nodes
- Rotating IP abuse tools
Bot operators also mix in residential proxies and human-assisted form spam. Simple CAPTCHAs are not enough. A layered defense is required: IP intelligence, behavioral filters, and rate-limits.
Effective Ways to Block VPN & Data Center IPs in MetForm
You have two practical methods:
- Use OOPSpam Anti-Spam plugin
- Use Cloudflare Firewall Rules (for Cloudflare users)
Both approaches filter hidden bot traffic and protect your form leads.
Method 1: Block VPN & Data Center IPs with OOPSpam (Recommended)
OOPSpam (that’s us 👋) offers the simplest and most automated way to block VPNs and data-center traffic in MetForm. It works directly inside WordPress and silently filters submissions before they reach your inbox.
Use this if: you want a plug-and-play solution without maintaining manual firewall rules.
Enable OOPSpam Protection for MetForm
Go to Plugins → Add New. Search OOPSpam Anti-Spam,install and activate.
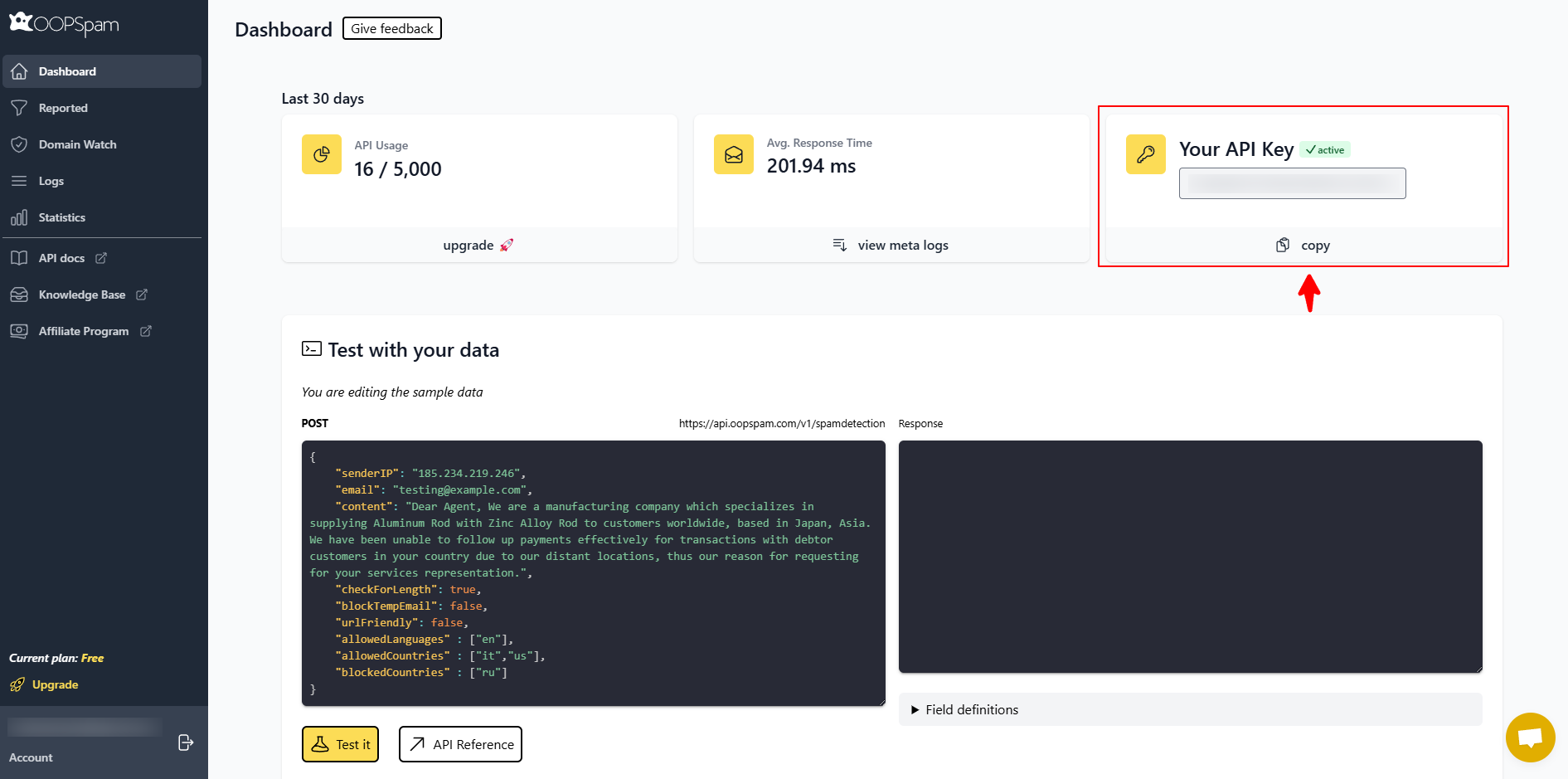
Create an account on the OOPSpam dashboard and copy your API key.
Go to WordPress Admin → OOPSpam → General Settings and paste your key.
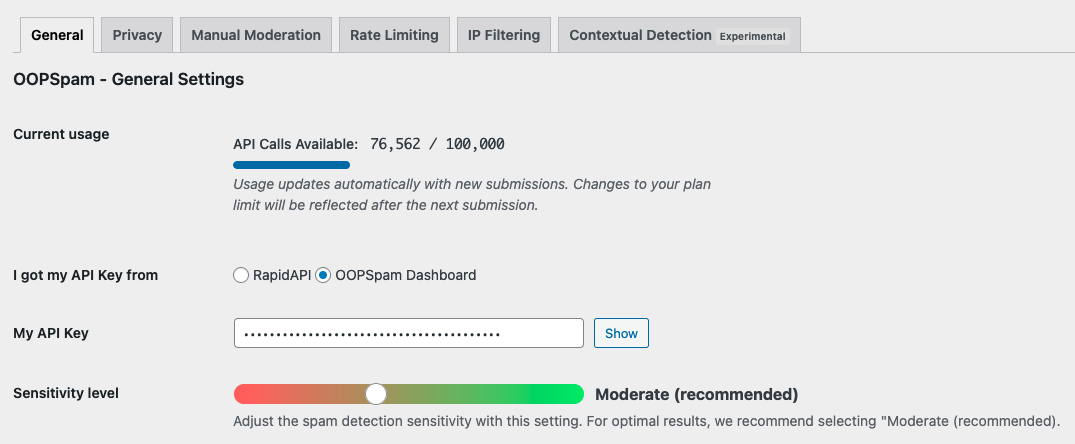
Turn on MetForm Spam Protection and click Save Changes.
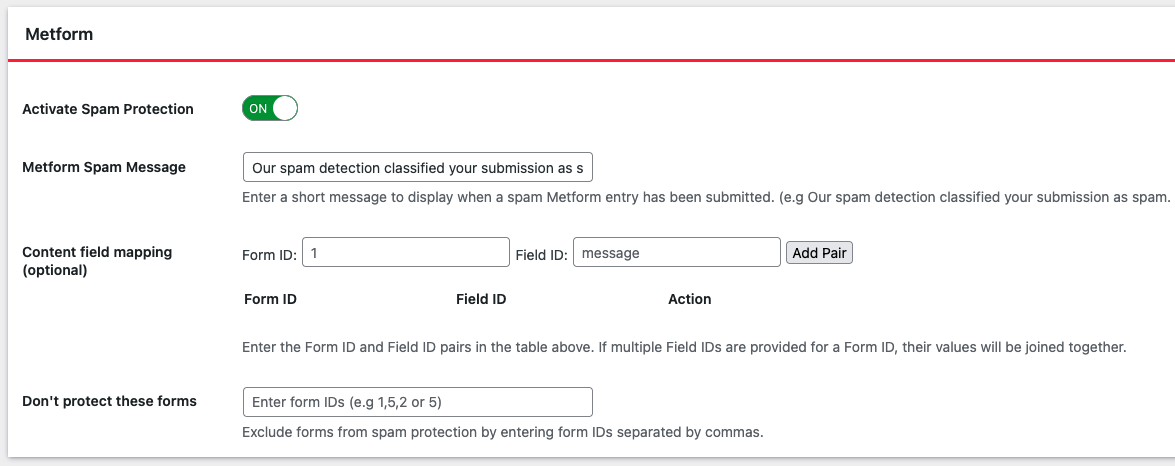
Enable VPN & Cloud-Server Blocking
Inside OOPSpam settings and open the IP Filtering tab:
- Turn on Block VPNs
- Turn on Block Cloud Providers
- Save
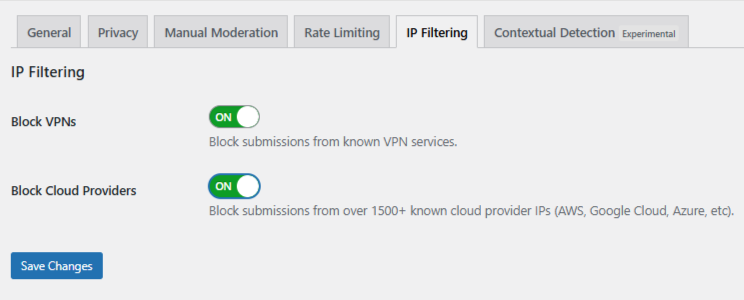
OOPSpam will now:
- Detect VPN traffic
- Detect server farm IPs (AWS, Google Cloud, etc.)
- Filter proxy/TOR submissions
- Apply ML-based spam scoring
- Provide logs for review
OOPSpam works automatically, so you don’t have to maintain IP lists or tune firewall rules. When you need control, you can switch to manual moderation and add your own allow/block IP rules. This keeps routine filtering hands-off while giving you moderation options when cases are borderline.
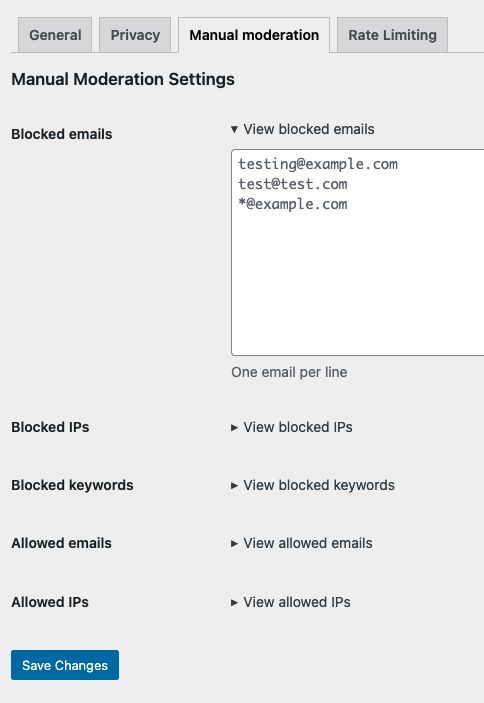
Method 2: Block VPN & Data Center IPs with Cloudflare Firewall
Cloudflare blocks suspicious traffic before it reaches your site. This is useful if you already use Cloudflare and want network-level filtering.
Create Firewall Rules
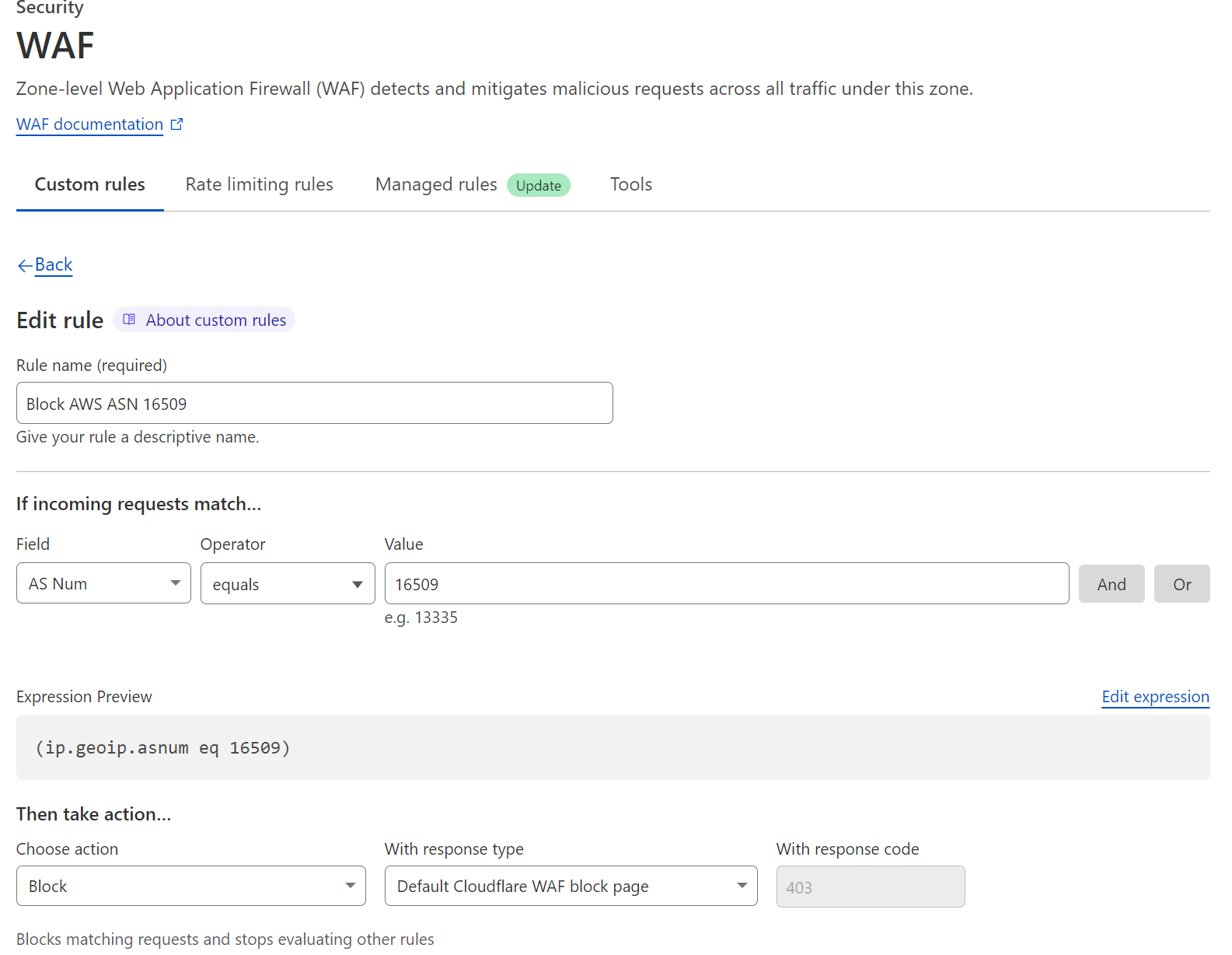
- Log in to Cloudflare
- Select your website
- Go to Security → Security rules
- Click Create Rule
- Name the rule: Example: Block AWS ASN 16509
- Rule condition example:
-
- Field: AS Num
- Operator: equals
- Value: 16509 (AWS ASN)
Expression preview example: (ip.geoip.asnum eq 16509)
- Action: Block (or Challenge first if testing)
- Save
This rule blocks requests from AWS data-center IPs, a common source of automated spam traffic.
Cloudflare gives powerful edge-level control. However, it requires tuning. If you want automatic VPN & data-center filtering with no manual rules, OOPSpam is easier.
Best Practice: Use Both Layers if Possible
For the best results:
| Layer | Purpose |
|---|---|
| Cloudflare WAF | Blocks anonymous networks before they reach WordPress |
| OOPSpam | Advanced form-level filtering + ML scanning + rate limiting |
This combination stops automated abuse and human-assisted spam.
Final thoughts
As bots adopt anonymous networks and automation tools, advanced filtering is necessary. Use OOPSpam for reliable plug-and-play protection, and add Cloudflare Firewall Rules if you need deeper control at the network edge. This simple configuration protects your forms, keeps your inbox clean, and preserves legitimate leads.