
Chazie Baniquid
Technical Content Marketer
6 minutes to read
How to Block VPN and Data Center IP Submissions in Avada Forms?
Avada Forms cannot block VPN or data center IPs on its own. The fastest, most reliable way to stop those submissions is to add OOPSpam to Avada Forms and enable its IP Filtering (Block VPNs + Block Cloud Providers). For extra protection, keep Avada’s Honeypot and Cloudflare Turnstile on, and if you use Cloudflare, add a simple WAF rule that challenges low bot-score traffic. This layered setup cuts spam without breaking real user flows.
Why VPN and Cloud IPs Flood Avada Forms
- VPNs hide true locations and rotate identities, letting abusers bypass basic rate limits.
- Cloud/data-center hosts (AWS, Google Cloud, OVH, DigitalOcean, etc.) power most automated bots; they are cheap, fast, and disposable.
Blocking these two sources won’t stop every bad actor, but it removes a large, noisy slice of anonymous traffic before it reaches your inbox or CRM.
What Avada Forms Can and Can’t Do Natively
A quick baseline helps you pick the right controls.
- Available out of the box:
-
- Honeypot element (stops simple bots).
- Cloudflare Turnstile element (privacy-friendly challenge; better UX than legacy captchas).
- Not available out of the box:
-
- IP reputation or ASN filtering (e.g., “block VPNs,” “block cloud providers”).
- Country allow/deny rules or per-form rate limiting with analytics.
To block VPN and data center IPs, you need a third-party plugin or an edge firewall. The most direct option for Avada Forms owners is OOPSpam (that’s us 👋).
Why OOPSpam Is the Straightforward Choice for Avada
Pick the tool that gives you results in minutes, not days.
- One-click IP Filtering: Toggle Block VPNs and Block Cloud Providers—no ASN lists to maintain.
- Always-updated reputation data: Covers 1,500+ data centers, known VPN/proxy ranges, and newly seen threats.
- Form-level controls: Works directly with Avada Forms. You can fine-tune per form without touching code.
- Layered defense built in: Rate limiting, ML-based scoring, keyword/context checks, and country rules to catch abuse that sneaks past IP filters.
- Quiet UX: Filters run in the background; legitimate users don’t see puzzles unless you choose to challenge them.
Step-by-Step: Enable OOPSpam on Avada Forms
Follow this once. It’s quick and repeatable across sites.
In WordPress → Plugins → Add New, search OOPSpam Anti-Spam. Install and activate.
Create an OOPSpam account and generate your API key.
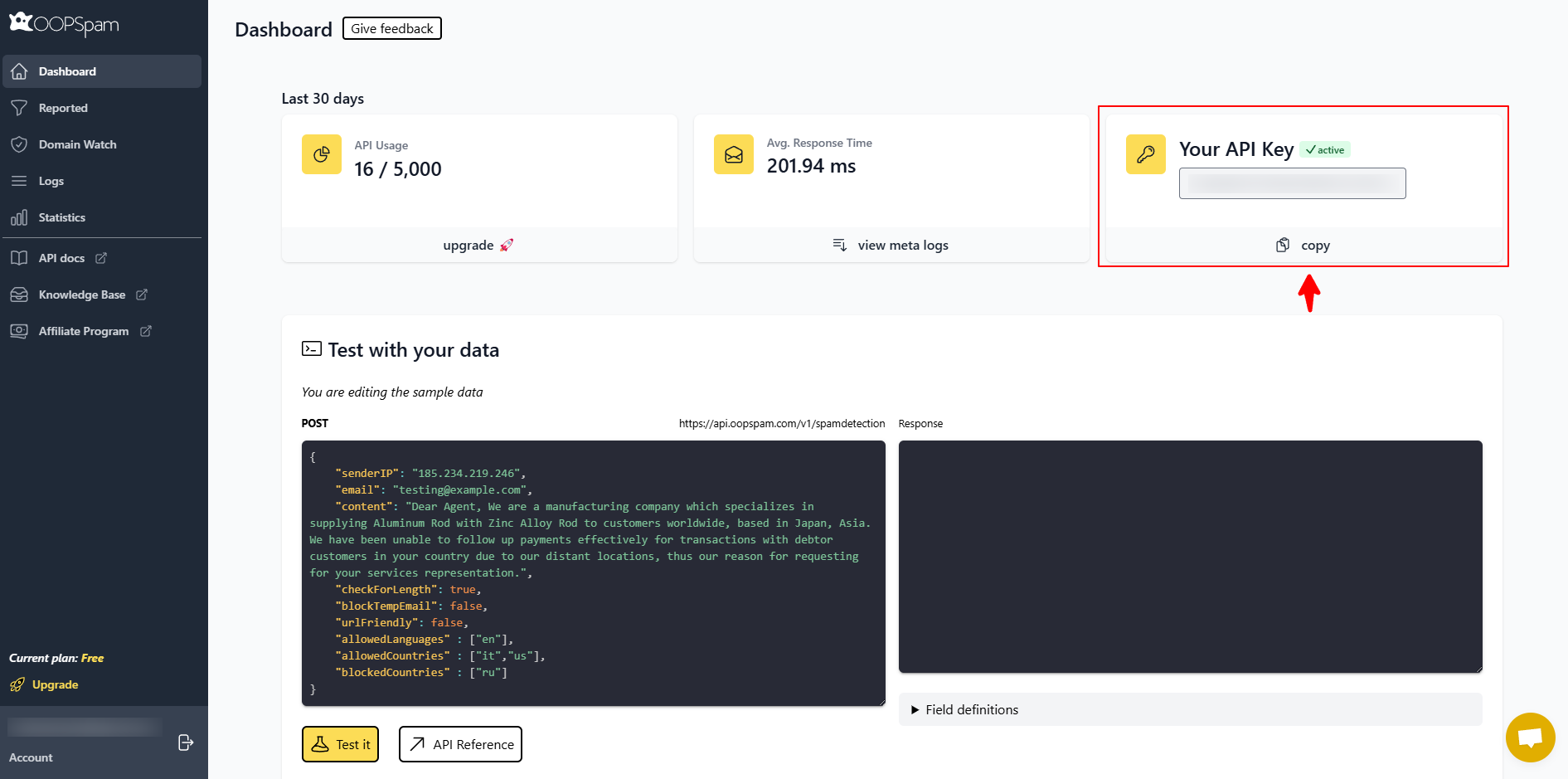
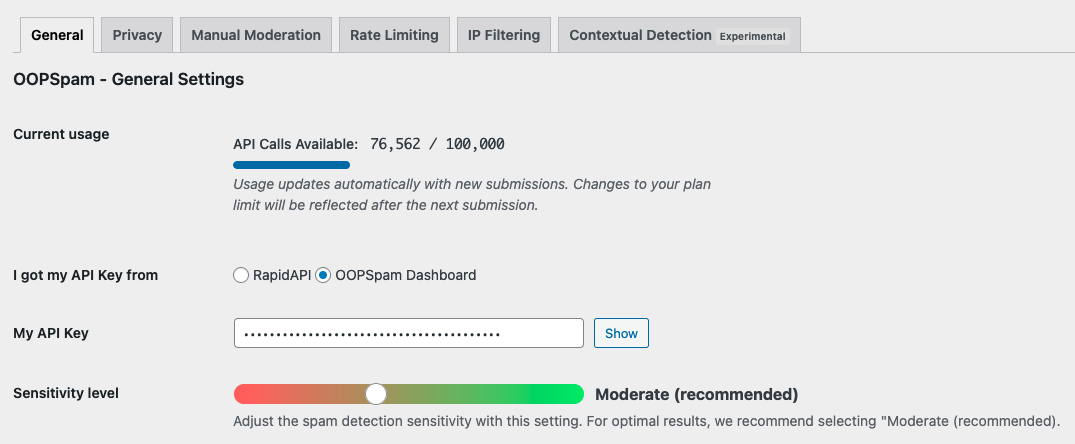
Go to Settings → OOPSpam Anti-Spam → General. Select OOPSpam Dashboard as the data source, paste your API key from the OOPSpam dashboard, and save.
Once OOPSpam detects Avada Forms, a dedicated section appears. Enable Activate Spam Protection. Optionally set a custom message for blocked submissions.
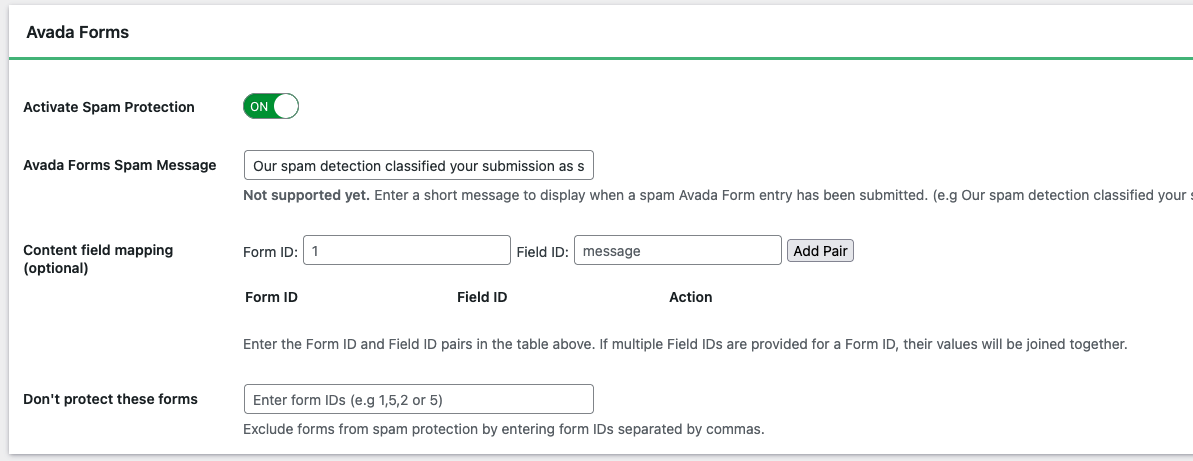
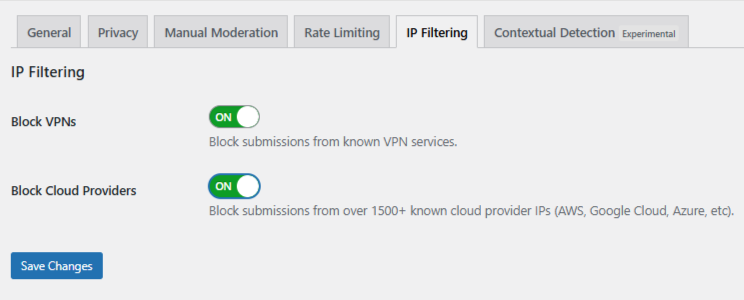
Open the IP Filtering tab and toggle:
- Block VPNs
- Block Cloud Providers (recommended)
(Optional) Add precision controls
- Rate limiting: Set per-form submission caps to slow “human-like” spam.
- Country rules: Allow or deny specific countries if your audience is regional.
- Keyword rules: Flag or block obvious spam phrases unique to your niche.
Submit your form in an Incognito window. Confirm outcomes in Spam & Ham Logs and in your OOPSpam Dashboard.
Keep Avada’s Honeypot and Turnstile elements enabled. They complement OOPSpam and improve accuracy with minimal friction.
Cloudflare WAF (Optional but Powerful)
If your site runs behind Cloudflare, block or challenge bad traffic before it hits WordPress.
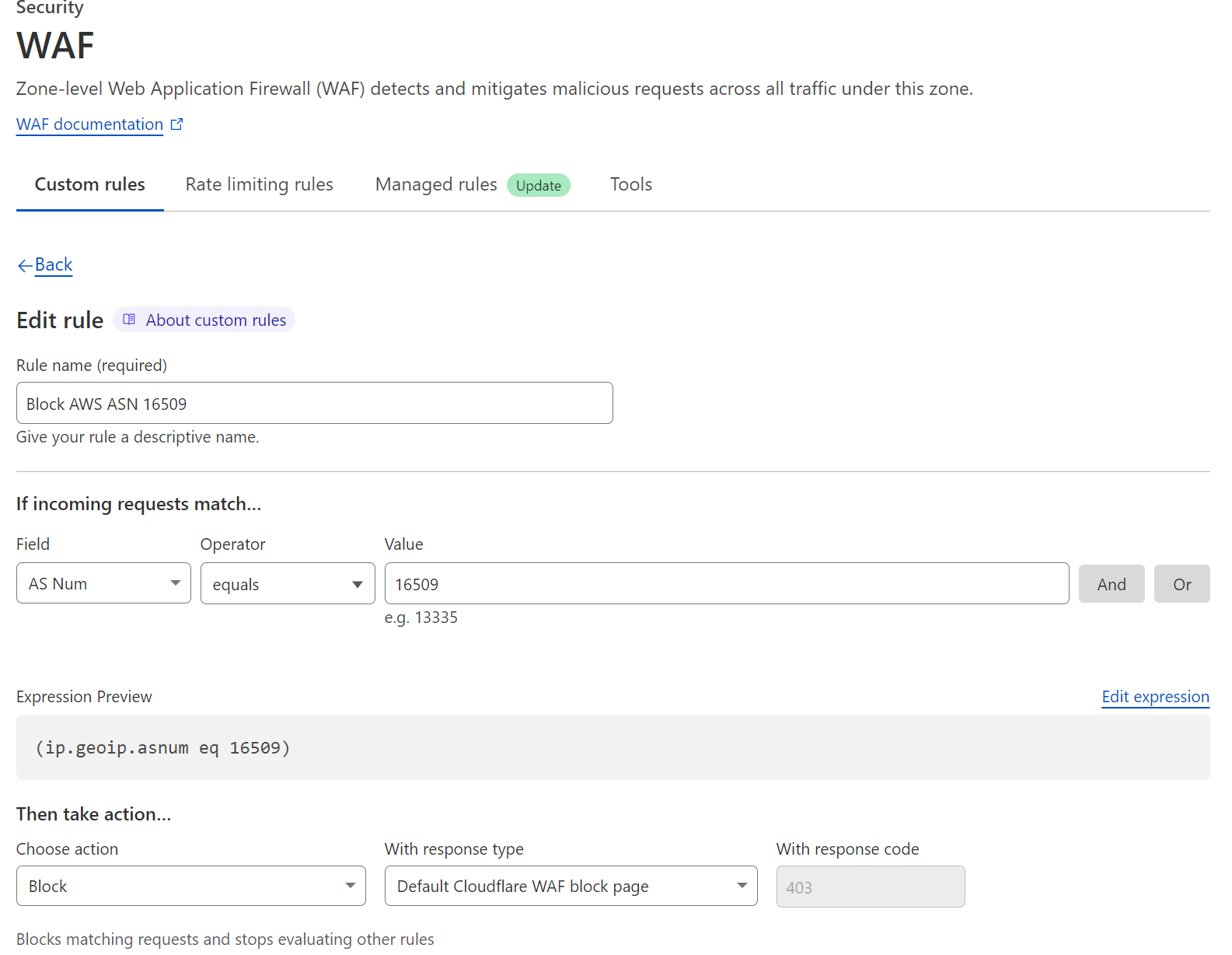
- Bot Score Rule: Set this expression —
cf.bot_management.score lt 30 and not cf.bot_management.verified_bot. Choose Managed Challenge as the action, or Block if the attack is severe. - ASN Rules: Keep a list of abusive networks (like specific hosting providers). Block or rate limit them temporarily, then review daily.
- Country Rules: If you don’t serve certain countries, block them at the edge. Still, keep OOPSpam’s per-form country rules active for better accuracy.
This approach reduces server load and works perfectly with OOPSpam’s filtering inside Avada Forms.
Tuning for Conversions and Fewer False Positives
You want to block abuse without hurting real users. This is how.
- Start conservative: Block Cloud Providers; challenge or allow + flag VPNs until you trust your pattern.
- Maintain allowlists: Add staff, agencies, and API partners so their submissions are never blocked.
- Watch the logs, not just volume: Check OOPSpam’s Spam/Ham logs weekly to spot patterns (countries, ASNs, or URLs) and adjust rules.
- Verify suspicious IPs: You can use tools like IP Reputation Check to determine whether a specific IP address is associated with a VPN or data center.
- Don’t over-block globally: Broad ASN blocks can catch remote workers and B2B users. Use them only during active incidents and remove them when quiet.
- Accessibility matters: Turnstile is friendlier to assistive tech than image puzzles. Keep it on with the Honeypot for baseline protection.
Final Thoughts
You don’t need a security team to stop VPN and data center spam on Avada. Turn on Avada’s Honeypot and Turnstile, add OOPSpam and enable Block VPNs + Block Cloud Providers, and, if available, apply a simple Cloudflare bot-score challenge. This layered setup is fast to deploy, low-maintenance, and highly effective. Keep an eye on the logs for a week, fine-tune your allow lists, and enjoy quieter inboxes and cleaner analytics.