
Chazie Baniquid
Technical Content Marketer
3 minutes to read
How to Limit Form Submissions in Jetpack Forms?
Jetpack Forms are simple and effective for WordPress sites, but they don’t have a built-in feature to limit the number of submissions. If you’re running a contest, collecting event signups, or just trying to stop repeated spam, you’ll need extra tools.
The best way is to combine OOPSpam Anti-Spam with Cloudflare’s rate limiting. Together, they give you full control over who can submit, how often, and from where.
Why Limit Submissions in Jetpack Forms?
Forms attract not just users, but also bots. Left unprotected, they can flood your database, skew survey results, and overwhelm your inbox. Limiting submissions helps:
- Reduce spam and repeated attempts.
- Protect site performance.
- Keep your data clean and fair.
Advanced Submission Control with OOPSpam
Jetpack already filters basic spam using Akismet, but OOPSpam (that’s us 👋) takes protection much further. It adds advanced rules to stop bots before their entries reach your inbox.
With OOPSpam, you can:
- Limit submissions by IP or email per minute/hour.
- Allow or deny specific countries.
- Block suspicious language patterns.
- Detect VPNs, proxies, and TOR users.
- Review logs to see what’s being blocked.
Setting Up OOPSpam for Jetpack Forms
Install and activate OOPSpam Anti-Spam from the WordPress plugin directory. Create an account with OOPSpam and copy your API key.
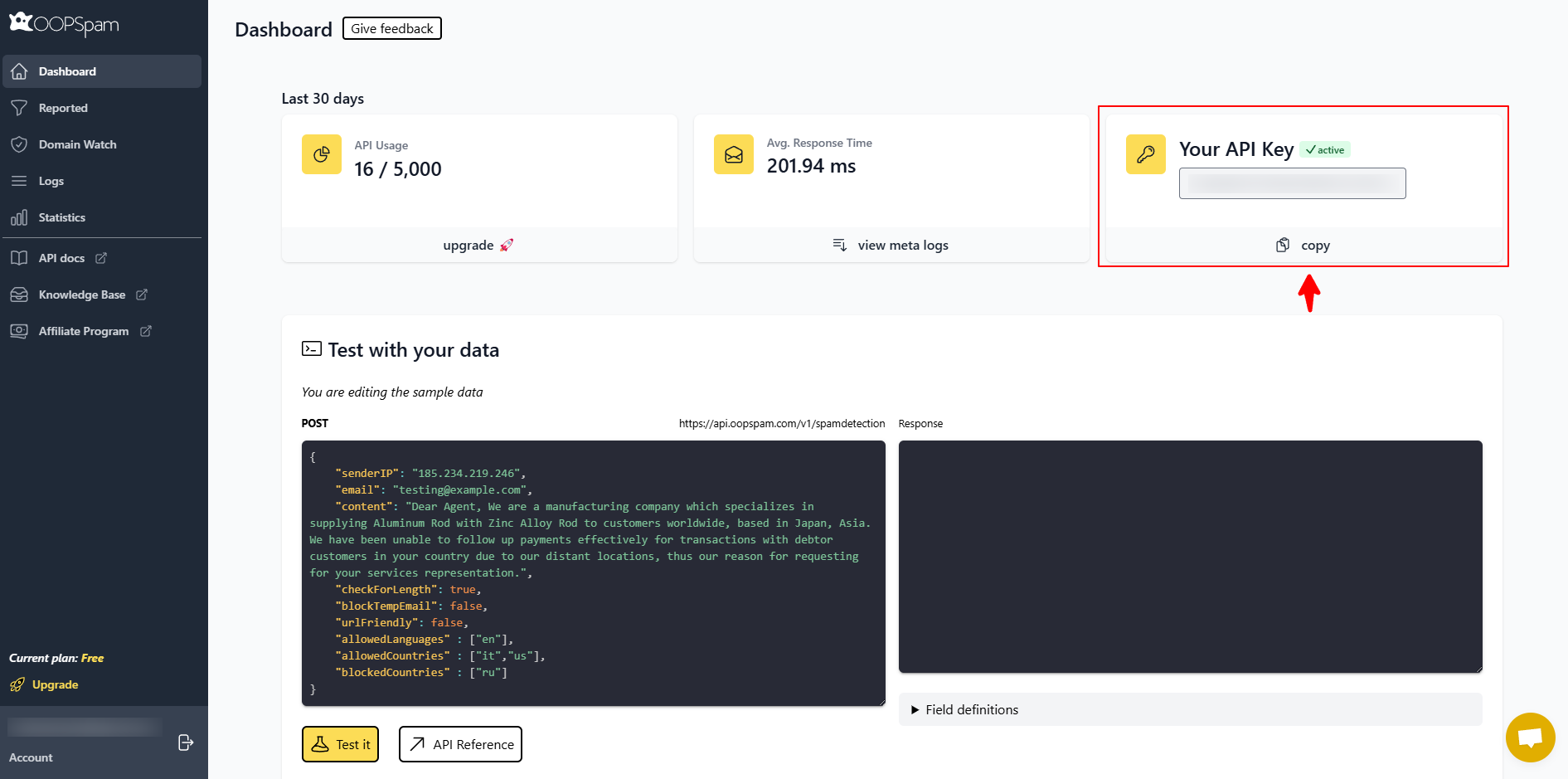
In WordPress, go to OOPSpam → General Settings and paste in your key.
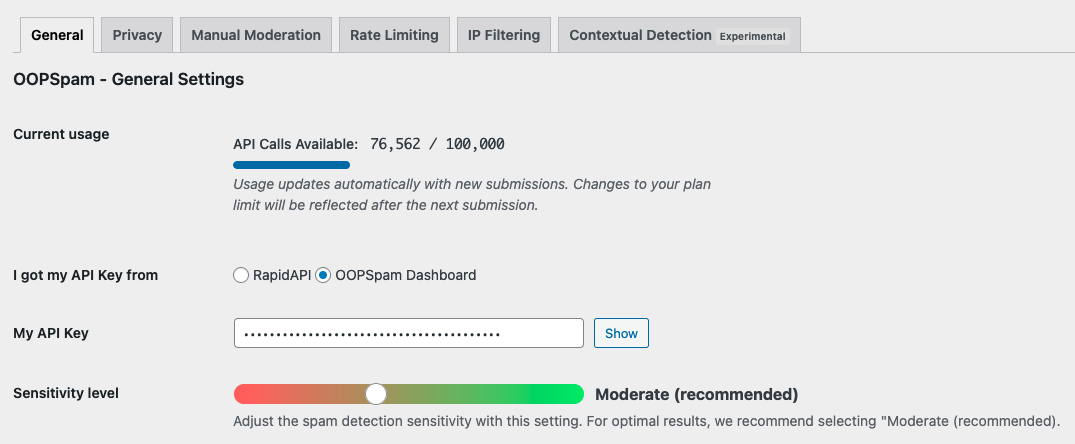
Toggle on spam protection so it covers your Jetpack forms.
Now go to Rate Limiting Settings. Turn on Enable Rate Limiting.
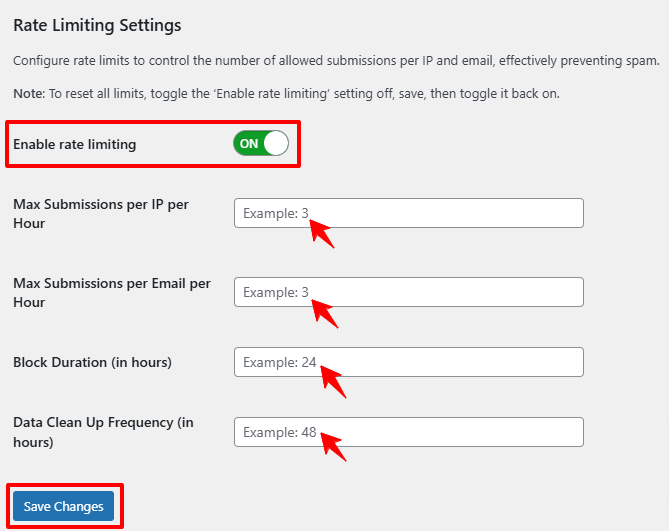
Here you can configure:
- Max submissions per IP/hour (e.g., 8/hour).
- Max submissions per email/hour (e.g., 3/hour).
- Block duration — How long to block once the limit is hit.
- Data clean-up frequency — Automatically clear logs.
Click Save Changes. Test by submitting multiple entries to make sure your thresholds work.
Firewall-Level Rate Limiting with Cloudflare
If your site runs through Cloudflare, you can add another layer of control at the network level. This stops abusive requests before they even reach WordPress.
Cloudflare’s WAF Rate Limiting lets you cap how many POST requests an IP can send to your form endpoint within a set timeframe.
Example setup:
- Rule: Limit POST requests to /wp-admin/admin-ajax.php (used by Jetpack Forms).
- Condition: Allow 3 requests per 10 minutes per IP.
- Action: Block or Challenge once the limit is exceeded.
This method is powerful because it prevents brute-force spam at the firewall level, keeping unnecessary traffic away from your server.
Final Thoughts
Jetpack Forms doesn’t include built-in submission limits, but you can still stay in control.
- Use OOPSpam Anti-Spam to apply advanced filters, block repeat entries, and catch bots.
- Add Cloudflare rate limiting to stop abusive requests before they hit WordPress.
Together, these tools give you fairness, stronger spam protection, and a smoother experience for genuine users.