2025 marked a dramatic shift in online spam tactics. While traditional spam continued, residential proxy networks emerged as the infrastructure of choice for attackers, making malicious traffic nearly impossible to trace. We also observed unprecedented card testing attacks targeting e-commerce checkout systems.
In this 2025 Annual Spam Report, we analyze the rise of residential proxies, evolving spam patterns across industries, and new attack vectors that emerged this year. For comparison with previous trends, see our 2024 Annual Spam Report.
✨ Key Findings
- Card testing attacks surged dramatically: we blocked over 450,000 attack attempts in a single week, the largest we've ever recorded.
- Residential proxies became the primary attack vector for all types of web spam, from contact form abuse to card testing. Attackers route traffic through compromised home devices, making detection extremely difficult.
- The United States leads spam origin at 44%, followed by Brazil (23%), China (16%), India (11%), and UK (6%).
- Gmail accounts for 63.21% of email addresses used in card testing attacks, followed by Yahoo (15.05%) and Microsoft services (16.01% combined).
- E-commerce spam jumped to 22% (up from 15% in 2024), driven primarily by card testing attacks on WooCommerce stores.
- Marketing and advertising spam now leads at 31.5%, with AI service promotions becoming a significant portion of unwanted messages.
- WordPress remains the top target at 61% of CMS-based spam, though its share decreased from 69% as attackers diversified.
- Our analysis sampled 25,654,124 spam IPs, a 34% increase from 2024, reflecting the growing scale of automated attacks.
The Year Card Testing Exploded
Card testing attacks emerged as a significant threat in 2025. These attacks involve fraudsters validating stolen credit card information against live e-commerce checkout systems, affecting thousands of online stores.
In September 2025, we observed and blocked the largest card testing attack wave in our history: over 450,000 attempts in just one week. Attackers targeted WooCommerce stores using both Classic and Block-based Checkout. PayPal was the most targeted payment gateway, but credit and debit card processors were also exploited.
How Card Testing Works
Card testing is a form of fraud where criminals use automated bots to verify whether stolen credit card details are valid. They submit small transactions or checkout attempts across multiple e-commerce sites, observing which cards get approved versus declined.

The geographic distribution of card testing attacks reveals a distinct pattern from general spam:
- USA (36%)
- Brazil (21%)
- UK (14%)
- Venezuela (12%)
- Philippines (11%)
- Colombia (6%)
How Attackers Bypassed Security
Modern card testing attacks exploit gaps in e-commerce platforms. WooCommerce's newer Block-based Checkout uses different code paths than classic checkout, and many security tools weren't designed to monitor both. Attackers took advantage by:
- Using API-first paths that bypass traditional hook-based security checks
- Exploiting Express Checkout shortcuts that connect directly to payment processors
Impact on Merchants
Card testing attacks cause cascading damage to online businesses:
- Payment processor penalties
- Email reputation damage
- Operational overload
- Financial losses
Public Email Providers in Web Spam
Spammers rely heavily on public email providers when submitting fake form entries, whether for card testing, contact form spam, or fake account registrations. Our analysis of blocked spam submissions revealed a striking concentration:

- Gmail (63.21%)
- Yahoo (15.05%)
- Hotmail.com (8.35%)
- Outlook.com (6.03%)
- Hotmail.co.uk (1.63%)
- Other providers (5.73%)
Microsoft email services combined (Hotmail.com, Outlook.com, Hotmail.co.uk) account for 16.01% of blocked emails. The top 5 providers represent 94.27% of all spam email addresses.
These email addresses appear across all types of spam: card testing attempts, contact form abuse, fake account registrations, and review spam. Since most major email providers don't offer reliable email verification APIs, it's difficult to determine whether these addresses are real accounts or randomly generated strings. The prevalence of free email providers is expected given their accessibility and the ease of creating multiple accounts.
Residential Proxies: The Invisible Attack Infrastructure
The most significant shift in 2025 was the widespread adoption of residential proxies across all types of web spam. Unlike datacenter IPs that are easy to block, residential proxies route malicious traffic through real home internet connections, making attackers appear as legitimate users. Whether submitting contact form spam, creating fake accounts, posting fraudulent reviews, or conducting card testing attacks, spammers increasingly rely on this infrastructure.
What Are Residential Proxies?
Residential proxies are IP addresses assigned to real home internet connections, including routers, smart TVs, security cameras, and other IoT devices. When attackers route their traffic through these devices, their requests appear to originate from ordinary home users rather than suspicious data centers.
According to research by Orange Cyberdefense and Sekoia.io, the residential proxy market has grown into a vast, interconnected ecosystem where legitimate-looking services often source their IP pools through questionable means, including malware infections and deceptive software bundling.
How Devices Become Proxies
Residential proxy networks acquire their IP pools through several methods:
- SDK integration in "free" applications
- Proxyware programs like Pawns.app and EarnApp
- Botnet infections on IoT devices
Scale of the Problem
The scale of residential proxy abuse has reached unprecedented levels. According to KrebsOnSecurity reporting on the Aisuru botnet, tracking service Spur.us observed 250 million unique residential proxy IPs in just 90 days, a figure described as "insane" and "unheard of."
Major botnet operators have shifted from DDoS attacks to residential proxy services because renting out infected devices provides steadier, more sustainable income than one-off attacks. This means the infrastructure powering card testing and spam is now larger and more resilient than ever.
Why This Matters for Spam Defense
Residential proxies fundamentally change the spam defense landscape:
- IP reputation is unreliable
- Geographic blocks are circumvented
- Rate limiting fails
- CAPTCHAs are bypassed
Defending against residential proxy attacks requires behavioral analysis, attribution-based rules, and multi-layered detection. In 2025, we introduced contextual spam detection that analyzes the context and characteristics of form submissions, making it significantly more effective at identifying malicious traffic from residential proxies.
The 2025 Spam Report
How We Collected and Analyzed the Data
This 2025 Annual Spam Report is based on a representative sample of 25,654,124 malicious IPs detected by OOPSpam throughout 2025. These IPs were flagged for engaging in spam activities targeting forms including sign-ups, reviews, contact forms, and e-commerce checkouts. The data focuses on online form spam, with special attention to the card testing attack patterns that dominated this year.
Data was gathered using machine-learning spam detection, behavioral analysis, and global network monitoring. We analyzed spam activity by geographic location, attack type, platform, and industry impact to identify actionable patterns.
Top Spam-Contributing Countries
The geographic distribution of spam shifted notably in 2025, with Latin America emerging as a major source alongside traditional spam hotspots.
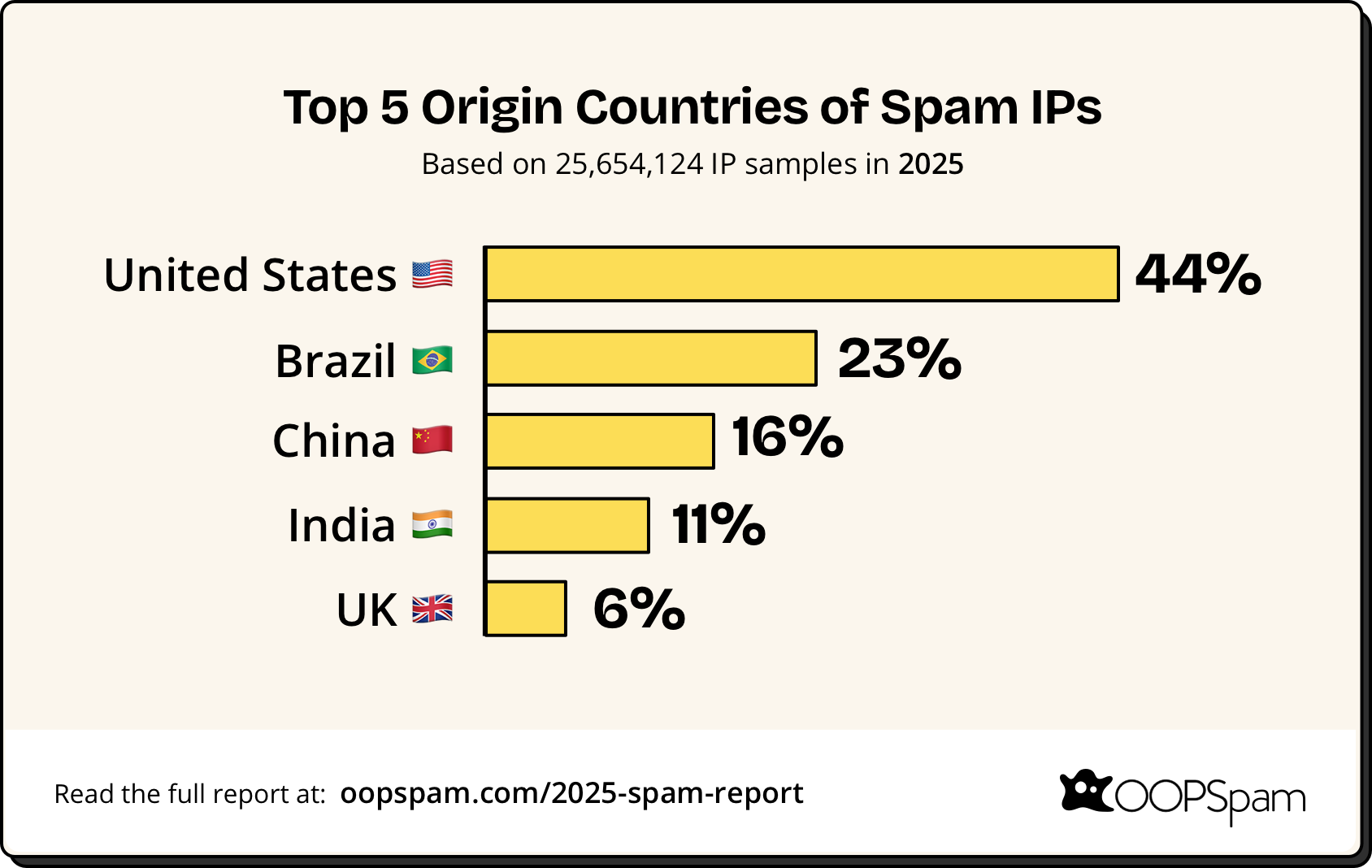
- United States (44%)
- Brazil (23%)
- China (16%)
- India (11%)
- United Kingdom (6%)
Together, these five countries account for 100% of our sampled spam IP activity, reflecting the concentration of spam infrastructure in these regions.
Spam by CMS Distribution
WordPress remained the primary target for spam, though its share decreased as attackers diversified across platforms.
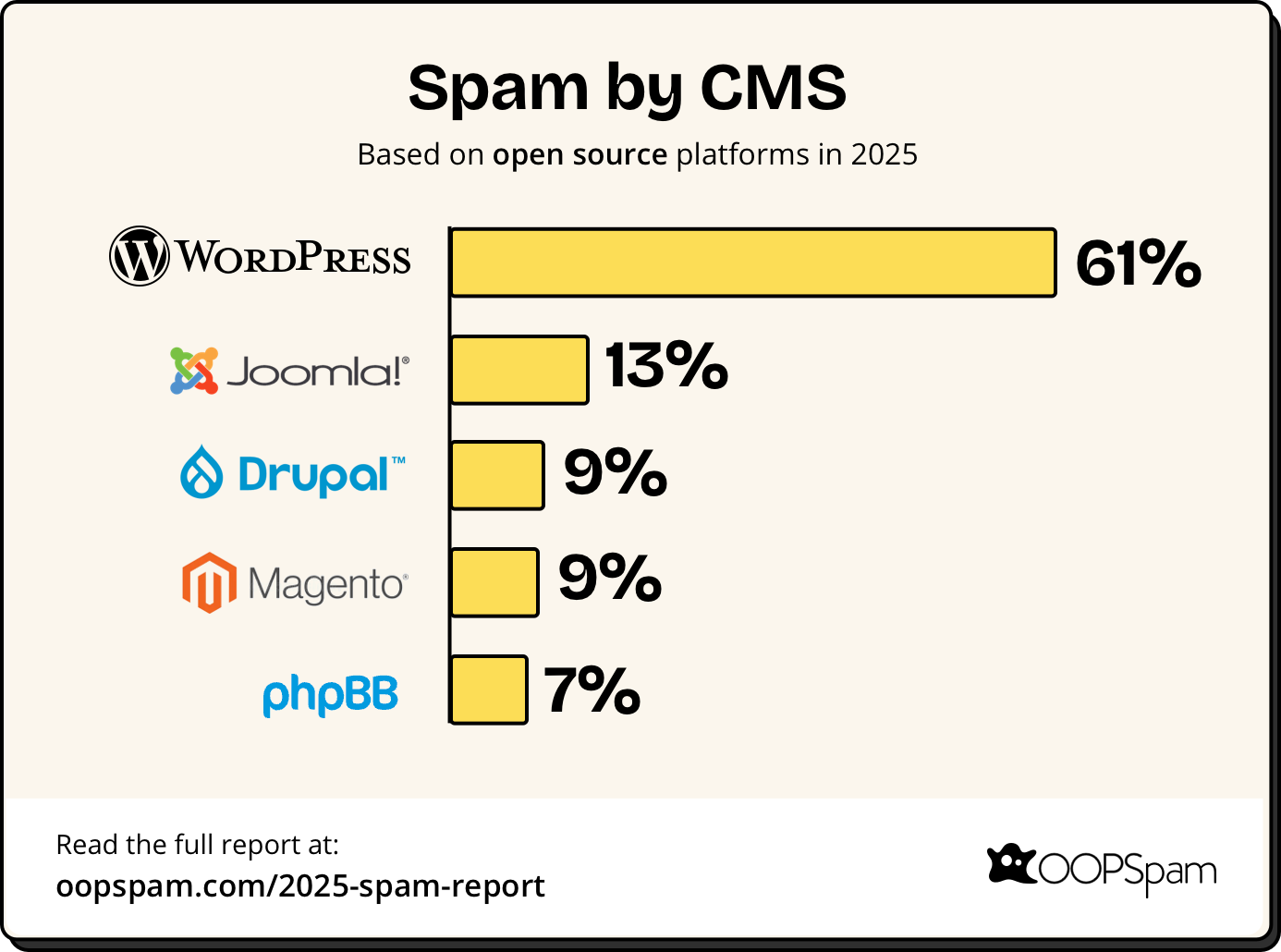
- WordPress (61%)
- Joomla (13.2%)
- Drupal (9.4%)
- Magento (8.9%)
- PHPBB (7.5%)
The shift toward Magento and e-commerce platforms reflects the broader trend of attackers targeting checkout systems and payment forms.
Most Spammed Forms
The distribution of spam across form types shifted significantly in 2025, with e-commerce forms seeing the largest increase due to card testing attacks.

- Sign-up forms (42%)
- Contact forms (26%)
- E-commerce forms (22%)
- Review forms (10%)
The 47% increase in e-commerce spam compared to 2024 directly reflects the card testing epidemic. During peak attack periods, some WooCommerce stores received thousands of fraudulent checkout attempts per hour.
Spam Types Breakdown
The content of spam messages evolved in 2025, with marketing spam overtaking health-related content for the first time.

- Marketing and advertising (31.5%)
- Health and medicine (25.3%)
- Adult content (18%)
- Finance (14%)
- Scam and fraud (8.5%)
- Others (2.7%)
The rise of AI-related marketing spam reflects the technology hype cycle. Every wave of innovation brings a corresponding wave of spam promoting services, courses, and tools.
Most Targeted WordPress Form Builders
Form builders for WordPress remain high-value targets, with Contact Form 7 continuing to lead. This is not due to security flaws, but due to its widespread adoption.
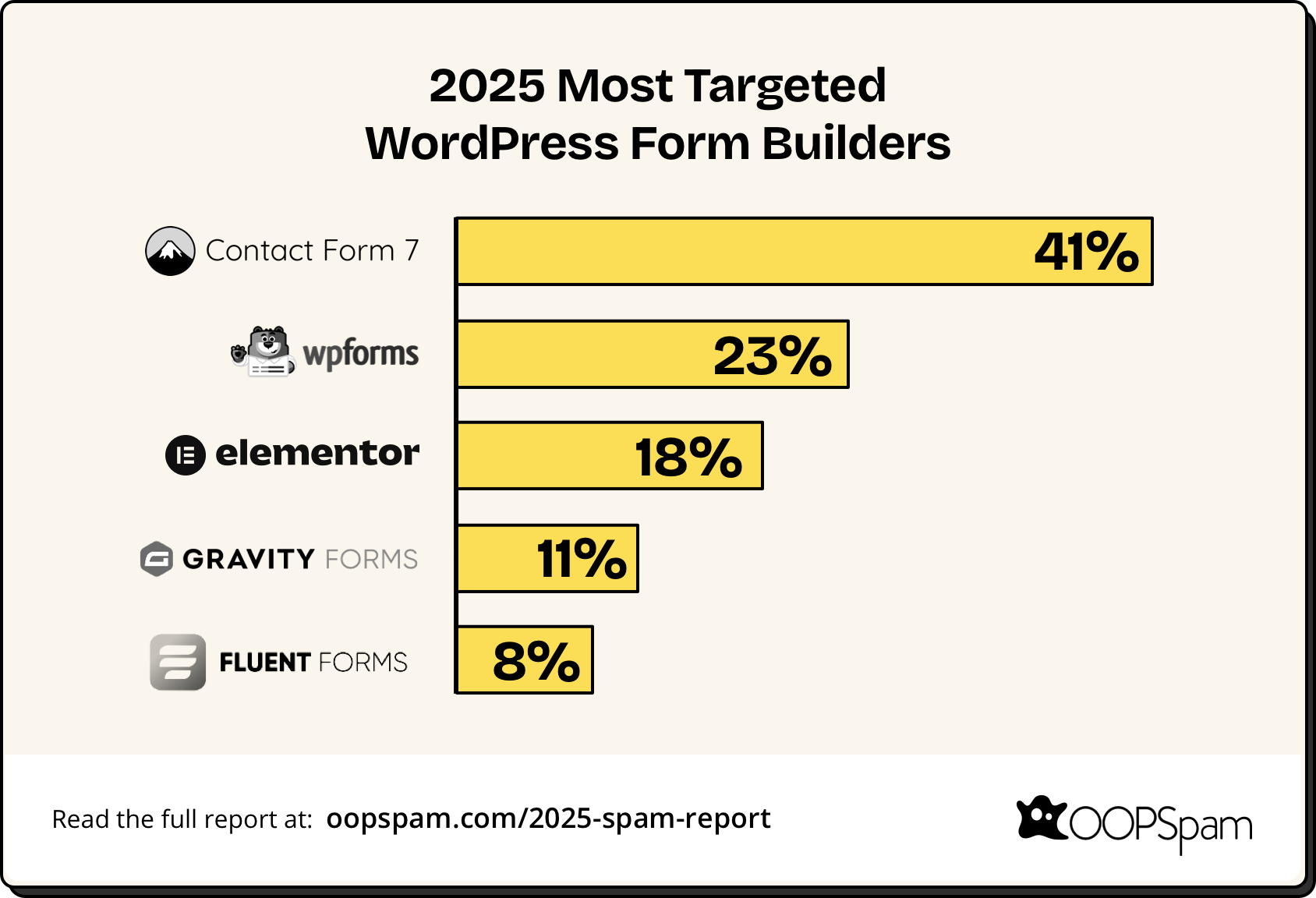
- Contact Form 7 (40.8%)
- WPForms (23%)
- Elementor Forms (17.7%)
- Gravity Forms (10.5%)
- Fluent Forms (8%)
Form builder popularity correlates directly with spam volume. This isn't about security weaknesses, but about where the targets are.
Most Abusive Data Centers
While residential proxies dominated attack traffic, traditional data center abuse continued. The 2025 data shows a shift in which providers are most exploited.
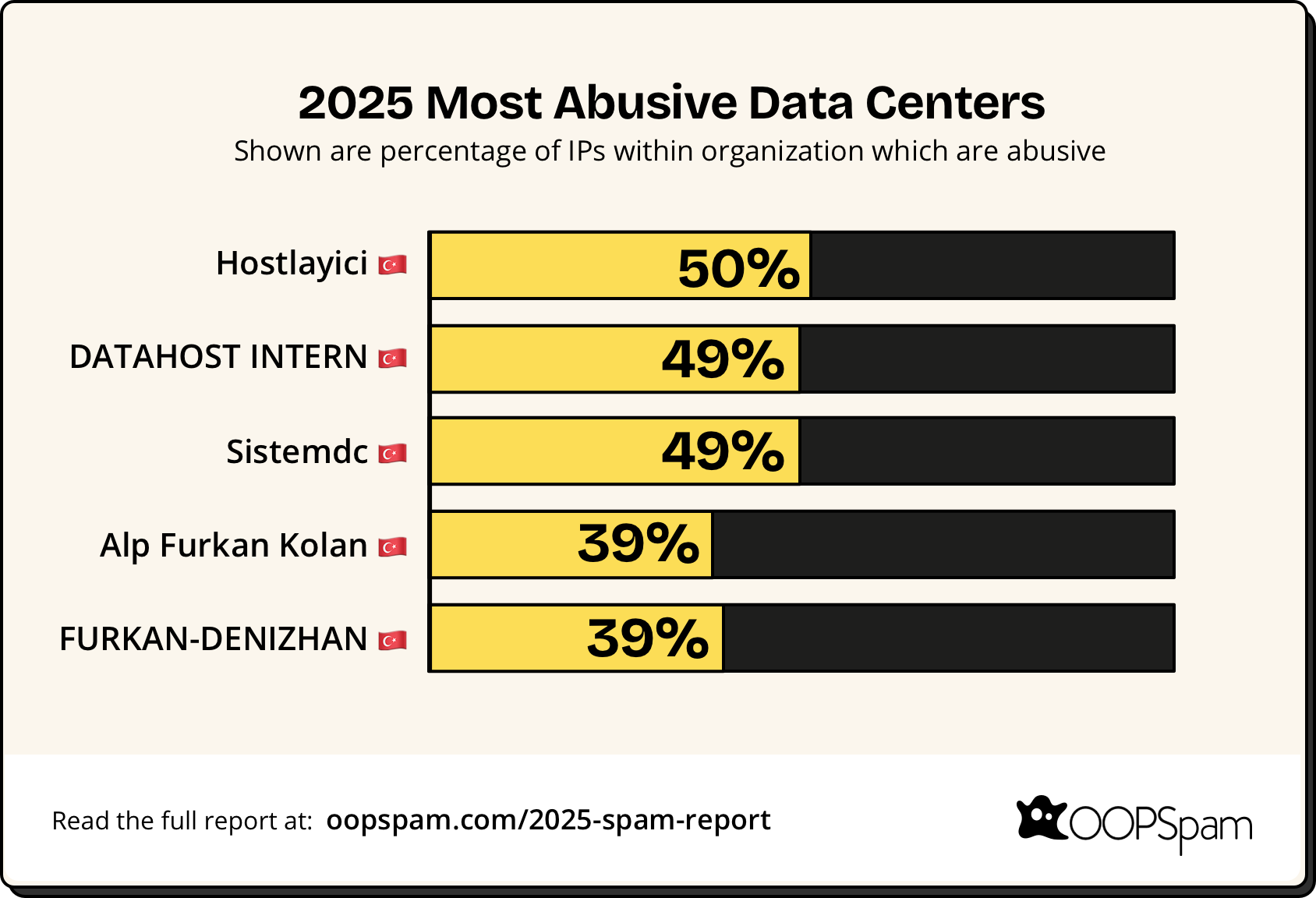
- Hostlayici (AS214382) - 50%
- Datahost Intern (AS60647) - 49.61%
- Sistemdc (AS211804) - 49.61%
- Alp Furkan Kolan (AS215620) - 39.26%
- Furkan-Denizhan (AS205795) - 39.06%
The concentration of abusive hosting in Turkey represents a shift from 2024, when different providers topped the list. This geographic clustering suggests organized spam operations taking advantage of regional hosting with lax enforcement.
However, these data center IPs represent a declining portion of attack traffic. The shift to residential proxies means blocking data center IPs is no longer sufficient protection.
Top 5 Domain Registrars with Spam Domains
Domain registrar abuse patterns shifted in 2025, with some registrars showing dramatically reduced spam domain counts compared to 2024.
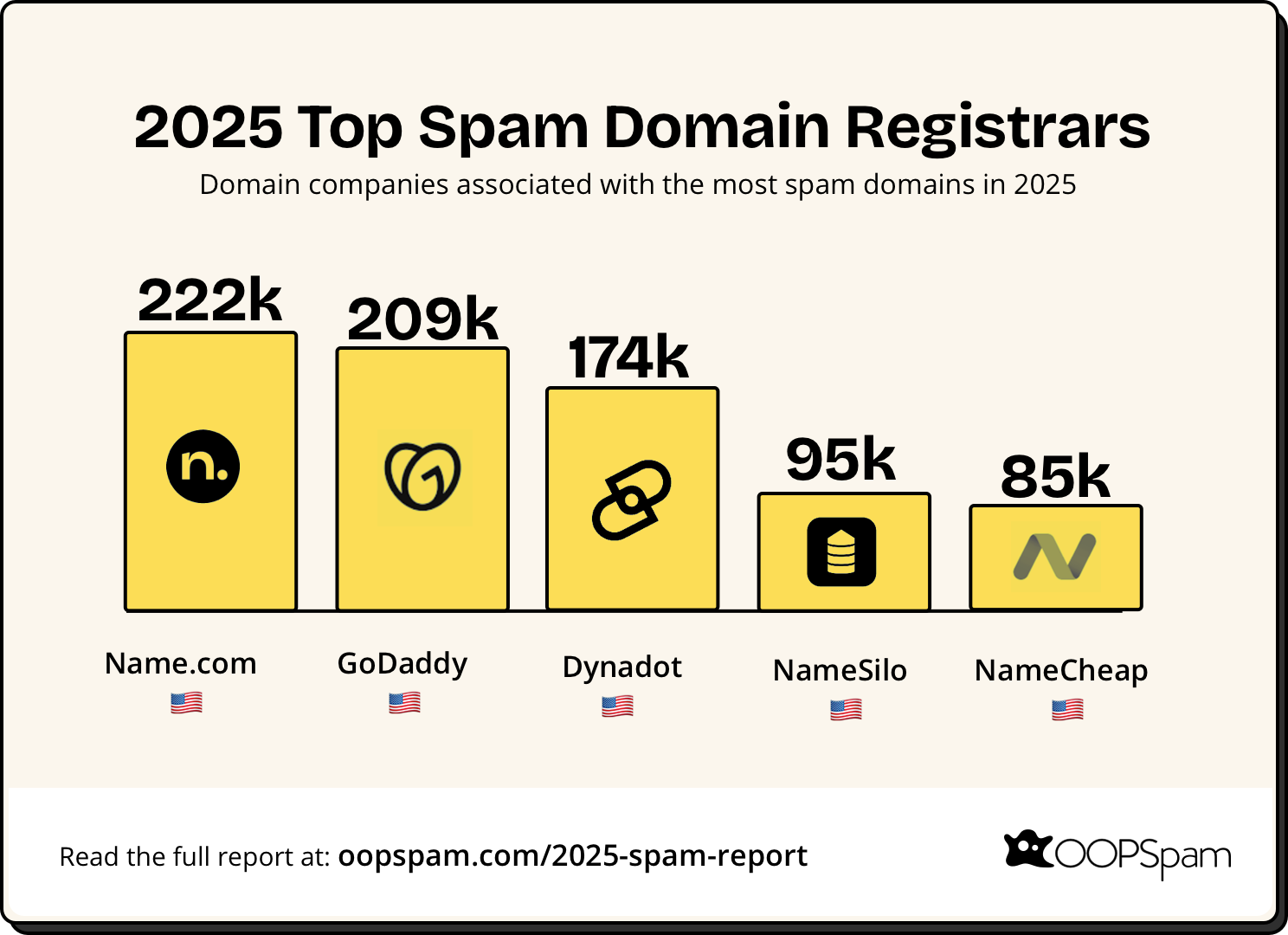
- Name.com (221,656 domains)
- GoDaddy (208,577 domains)
- Dynadot (174,110 domains)
- NameSilo (94,565 domains)
- Namecheap (85,439 domains)
The dramatic reduction in spam domain counts at major registrars suggests improved abuse detection and faster takedowns. However, we continue to detect aggressive spam domains from smaller registrars in China and Hong Kong being used for phishing and financial fraud.

Reflecting on 2025
2025 represented a fundamental shift in the spam landscape. Residential proxy networks became the infrastructure of choice for all types of web spam, from contact form abuse to card testing attacks. Traditional defenses built around IP reputation and geographic blocking are no longer sufficient.
The key lessons from 2025:
- Behavioral detection is essential: When attackers can appear from any IP, you must analyze behavior patterns including session characteristics, attribution data, and submission timing.
- Payment fraud is organized crime: Card testing isn't amateur activity. These are sophisticated operations with access to millions of proxy IPs and automated tooling.
- IoT security affects everyone: Every compromised router, camera, or smart device becomes a potential proxy node for attacking someone else.
- Platform-level protection matters: WooCommerce's Block-based Checkout created new attack surfaces that required new detection approaches.
Looking Ahead to 2026
Based on 2025 trends, here's what we expect in the coming year:
1. AI-Powered Attack Automation
Attackers will increasingly use AI to generate realistic form submissions, bypass CAPTCHAs, and create convincing phishing content. The arms race between AI detection and AI evasion will intensify.
2. Residential Proxy Growth
The residential proxy market will continue expanding, with more IoT devices enrolled through malware and deceptive software. Expect over 100 million active residential proxy IPs by year end.
3. Payment Fraud Evolution
Card testing will evolve with more sophisticated evasion techniques. Attackers will target newer payment methods including cryptocurrency payment gateways and buy-now-pay-later services.
4. Regulatory Response
Governments may begin requiring IoT security standards and holding manufacturers accountable for devices that become botnet nodes. The EU Cyber Resilience Act could set precedent.
5. Multi-Layer Defense Adoption
More businesses will adopt behavioral analysis and attribution-based fraud detection, moving beyond simple IP blocking and CAPTCHA-only approaches.
Final Thoughts
The spam landscape in 2025 became more sophisticated, more automated, and harder to detect. Residential proxies have fundamentally changed how attackers operate, enabling them to blend in with legitimate traffic across all types of web spam.
The good news: these attacks are beatable. Our success in blocking hundreds of thousands of spam attempts proves that behavioral detection, attribution analysis, and multi-layered defense work. The key is staying ahead of evolving tactics while maintaining protection that doesn't block legitimate users.
We remain committed to helping businesses defend against these threats. The battle against spam continues, but with the right tools and strategies, it's a battle we can win.